What is information rights management (IRM)?
Information rights management (IRM) is a discipline that involves managing, controlling and securing content from unwanted access. IRM is a subset of digital rights management (DRM), which protects multimedia content, including video and music.
Rights management technology restricts access to specific content, such as content with specific file formats, and ensures only authorized users can access protected content formats. DRM technology protects intellectual property and sensitive information from patent and copyright infringement and piracy. By contrast, IRM protects sensitive data, especially data that's exchanged with parties outside an organization, such as suppliers and partners.
IRM is an important element in the information content lifecycle, governing how information is protected. Popular productivity platforms and office applications such as Microsoft Office 365, including Word, Excel, Outlook, PowerPoint and SharePoint Online, have embedded IRM features to configure IRM rules for various file types. Office 365's cloud-based resources, such as those available with Microsoft Azure Rights Management System and Azure Information Protection deliver additional file protection
With increases in cybersecurity attacks and other unauthorized access events, information of all kinds must be actively protected. Effective data security and protection strategies prevent business disruptions, financial losses, destruction of business-critical data and damage to an organization's reputation.
How does IRM work?
IRM is part of broader digital asset management systems and processes that organize, store and retrieve rich media digital content. IRM differs from DAM: IRM establishes how digital assets are accessed and who can access them while DAM addresses how digital assets are collected, organized and stored for use by authorized individuals.
In practice, rights management services use encryption to protect sensitive documents and confidential information resources from unauthorized user access. IRM rules might permit viewing but prohibit copying and pasting of the content elsewhere or taking screenshots. IRM typically translates into specific rules that govern how documents can be accessed and used.
When a user requests access to a restricted document, authentication is required. The request goes to a special server that reviews a list of approved viewers; if the credentials match, the system issues a release license for access. The system might specify permissions, such as read-only or no copying. IRM apps create additional IT overhead with the associated costs that must be evaluated against perceived security threats.
IRM has some limitations. Implementing it often requires the use of specialized applications that encapsulate the content. IRM protection can be bypassed in several ways, such as hand-copying or retyping content, using screen capture features and by taking a photo of a document.
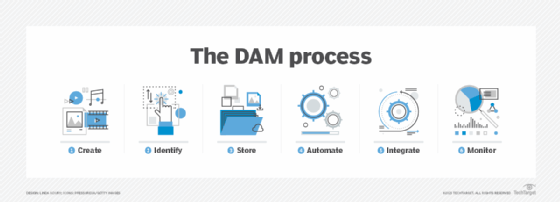
Components of an IRM strategy
An IRM strategy, along with related policies and procedures, addresses several data protection issues and provides a range of functionality, such as the following:
- Defining file use and file sharing attributes.
- Setting parameters for remotely accessing content.
- Defining access controls for documents and other content.
- Identifying how documents are tracked.
- Specifying how encryption is used.
- Defining who has access.
Why is IRM important?
There are several reasons IRM is an important consideration, including the following:
- Document types. IRM is critical to all sorts of enterprise document files, including Word documents, Excel spreadsheets and PowerPoint presentations.
- Security. It's a key part of a data protection strategy, protecting files from unauthorized viewing, copying, printing, forwarding, deleting and editing.
- Compliance. IRM helps organizations comply with data protection and security standards and regulations. For example, the European Union's (EU's) General Data Protection Regulation (GDPR) requires significant data protection capabilities.
- Audits. The ability to demonstrate information and data protection controls is an important IT audit consideration. Having an IRM policy with associated procedures and systems is important audit evidence.
- Broad protection. IRM-protected documents retain their protection regardless of where the files are located or how they're accessed.
Who uses IRM?
The need to protect and restrict access to certain kinds of information, such as document files and customer records, can justify the need for IRM technology. Any organization that has a data protection policy can benefit by using IRM.
For example, in healthcare, the Health Insurance Portability and Accountability Act (HIPAA) requires the protection of electronic protected health information (ePHI). IRM is combined with other document security practices to ensure patient data is protected.
Standards and regulations impacting IRM
Several standards and regulations support the use of IRM and DRM. Key regulations include the following:
- GDPR. This important EU-based regulation addresses many aspects of data protection, including IRM. It has significant penalties for noncompliance.
- HIPAA. While this legislation focuses primarily on the protection of protected healthcare information and ePHI, its data protection controls can be applied to nonhealthcare applications.
- Federal Information Security Modernization Act. FISMA is a key government security regulation. Its requirements can map to DRM and IRM to protect both unclassified and classified Information.
- Digital Millennium Copyright Act. DMCA dates to 1998 with requirements that protect content contained in videos, music, software, books and other intellectual property from unauthorized access, use and dissemination of such content.
- Data Protection Act of 2018. This United Kingdom legislation complements the GDPR. It mandates controls for all kinds of digital information processed in the UK.
- Personal Information Protection and Electronic Documents Act. Compliance with Canada's PIPEDA legislation can be implemented using DRM and IRM technology.
- California Consumer Privacy Act. CCPA protects the privacy of personal information.
- Sarbanes-Oxley Act. The Sarbanes-Oxley Act applies to all U.S. public companies and includes specifications for information protection.
Several standards that can be applied to IRM and DRM include the following:
- International Organization for Standardization (ISO)/International Electrotechnical Commission (IEC) 27001 specifies the creation and management of information security management systems, which address access control and privacy.
- ISO/IEC 27002 complements ISO 27001 by specifying how to define and implement information security controls that IRM and DRM technology addresses.
- ISO 15489 specifies the need for records management controls to protect document access and privacy.
- British Standard 10008-1:2020 provides specifications on protecting information stored on electronic information management systems.
- National Institute of Standards and Technology SP 800-53 addresses all aspects of information security and privacy controls, primarily for government use but is also applicable to nongovernment organizations.
Use cases for IRM
IRM focuses on electronic information and documents, so its use cases are mostly implemented using established applications such as Microsoft Outlook, Word, Excel and PowerPoint.
These applications have built-in security measures to establish how files are protected from unauthorized access. Security capabilities include setting up permissions, launching password protection, restricting who can edit a file, limiting the type of access a person has and adding a digital signature. Additional functions for file sharing managing versions are available.
Implementing an IRM policy and application
Policies governing the lifecycle of information, from creation to disposal, are essential. They demonstrate an organization's commitment to data protection and data privacy. IRM policies are usually embedded in an enterprise information security policy. The following are key components of an IRM policy template:
- What content is to be protected.
- The rules for accessing and securing the content.
- Who has access to the content.
- How IRM rules will be implemented, such as with software or other tools.
- Who can change IRM rules and when rules can be changed.
- Penalties for attempting to bypass IRM rules.
If a separate IRM tool is being needed, such as for special requirements like highly classified government documents, these steps should be followed:
- Determine the IRM capabilities required.
- Determine if existing IRM capabilities can provide a suitable approach.
- If no existing IRM capabilities are found, secure senior management approval for an IRM project.
- Define a project team and project plan.
- Evaluate IRM tools, including open source software, against the requirements and pick one.
- Perform tests of the IRM tool in a secure environment.
- Complete the implementation; launch production; train the administrators.
- Deliver user training and awareness of the new service.
- Schedule regular system performance reviews.
- Schedule audits to ensure compliance with applicable rules.
Advantages and limitations of IRM
IRM lets organizations protect files and content from unauthorized access and provides limited access when necessary. Other benefits include the following:
- Informing users of their rights. IRM ensures users know what they can do with their protected information.
- Ensuring ownership. IRM ensures authors their work won't be accessed, altered or rebranded by others.
- Ensuring data privacy. Use of IRM protects confidential user content from unauthorized viewing or interaction.
- Ensuring compliance. IRM technology helps ensure that protected content can demonstrate compliance with key requirements.
- Enabling sharing and collaboration. IRM ensures that the content is protected from any changes during sharing or collaboration, unless restrictions are suspended.
Limitations of IRM include the following:
- Security. Even with IRM, security can be bypassed or hacked. Additional security tools are needed to prevent viruses, malware, phishing and other attacks.
- Compliance. Organizations might have to implement DRM technology or other applications to demonstrate compliance.
- Controls. Monitoring and managing IRM controls may be time-consuming. Unless the security operations center or security team has expertise in access rights management, it can become a challenge to keep these controls up to date.
- Financial considerations. IRM software is an added cost that must be weighed against the benefits of protecting critical files.
Find out more about how digital asset management works and is used.






